SSH Tunnels
What you’ll learn: Use SSH tunnels to proxy your internet traffic and remotely access resources on your home network.
Prerequisites: Basic SSH experience, familiarity with using the command line, and comfort installing software on Linux using your default package manager (apt or yum).
Although “SSH” stands for “secure shell,” you can do a lot more with it. When connected to another computer via SSH, you’re logged in as a user as though you were in front of the machine. This means you can access its resources, including networking capabilities. This article assumes you’re familiar with using SSH to connect to remote machines and run commands in the terminal.
Let’s start with a simple example that’s actually two tips in one! If you want to browse a directory on your home computer, you can run the following Python one-liner:
python3 -m http.server
You will see this output:
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
You can now visit http://localhost:8000 on your computer to view a directory listing.
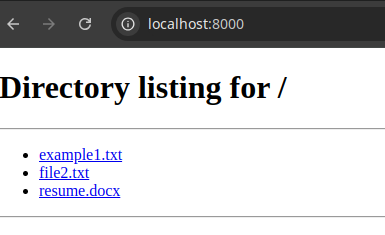
You can also go to the machine’s IP address from any other computer on your local network.
For example, http://192.168.1.100:8000.
This is handy for downloading files from a computer somewhere else in your house when you’re too lazy to walk over to it.
Accessing this remotely via SSH is super easy; barely an inconvenience! Instead of connecting to the device like this:
ssh myhost
Do this:
ssh -L 9999:localhost:8000 myhost
Then, from your remote computer, you can visit http://localhost:9999 and view the directory listing and even download the files.
The -L parameter specifies local forwarding.
Another option is -R (remote), which allows the other machine to access local resources on this machine.
Remote forwarding is a topic for another article, but knowing it exists gives more context to how “local” is being used here.
Let’s break 9999:localhost:8000 into two sections: 9999 and localhost:8000.
9999 specifies the port on your computer you will use to access the resource.
The localhost:8000 is from the perspective of the machine you’re connecting to.
It will share its localhost:8000 over the SSH tunnel, which you can view by navigating to http://localhost:9999.
You can (and usually will) use the same port number in both positions.
I only changed it here to make it less confusing.
Proxying Internet Traffic
You can use this forwarding trick to essentially create your own private VPN. Here are some reasons you might want to do this:
- You don’t trust the network you’re connected to.
- You want to have your browsing traffic come from your home due to geographical restrictions.
- Bypassing content filtering.
- Take advantage of privacy-protecting DNS active on your home network.
- Be protected by ad-blocking services on your home network.
- Troubleshooting a site problem by viewing it from a different location or ISP.
The simplest way to do this is to install squid, an open-source proxy service.
# Debian-based
sudo apt install squid
# Red Hat-based
sudo yum install squid
By default, squid runs on port 3128 on localhost.
Let’s connect to our home server again:
ssh -L 3129:localhost:3128 myhost
We’re using 3129 locally for illustration purposes.
You may also need to change the port if the remote port is in use locally by another application.
Now, let’s open a browser using the tunnel:
chromium --proxy-server=localhost:3129
Use a site such as jsonip.com to confirm that you’re seeing your home IP address.
SSH Configuration
Instead of extra typing every time you run ssh, you can just add the forwarding information to your ~/.ssh/config file:
host myhost
hostname 123.456.789
localforward 3129 localhost:3128
Browser Configuration
The --proxy-server trick can be used with Google Chrome and Chromium.
In Firefox, go to Settings > General > Network Settings > Settings to enter the proxy information:
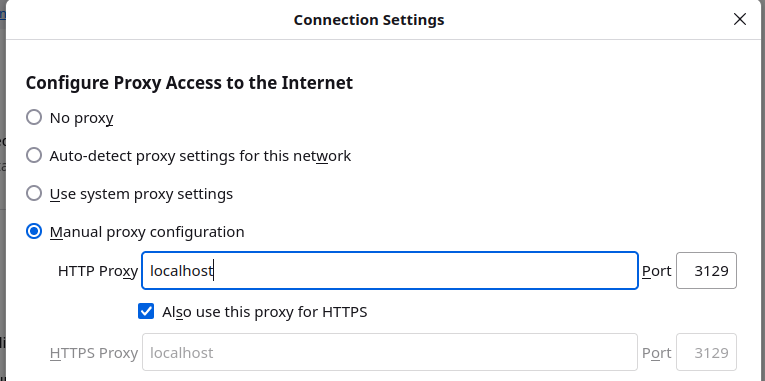
Save these settings and you will be browsing through your home network. If you’re a web developer and you set one browser to use the proxy and leave another with default settings, you can more easily troubleshoot certain issues.
Final Notes
You can use this method to access your home router settings, and anything else restricted to your private home network. One great example is the GUI for Syncthing. To learn more about Syncthing, please check out my book on Amazon.
If you have requests for future article topics, or want to hire me to write for you, please contact me at the e-mail address below.